Since I've enabled a "reject" DMARC policy on my domains, I've been reviewing the various failure reports that come in to see what crazy spam those crazy spamme…
Mashable's Chris Taylor talks about the problem of misdirected emails . A good read and it helps to expose a real issue that I don't think many people stop and consider. …
I've long had a little banner at the bottom of my xnnd.com DNS tools site that says "since 2008" but it looks like I'm going to have to change that. Looking th…
Remember this blast from the past? Back in 2007, email expert John Levine sat down with Canada's CBC News to be interviewed for what became "Spam, the Documentary."…
How do I keep my email messages out of Gmail's Promotional tab? This is a common question lately. Is there one common answer? Ask six different people, and you'll get six…
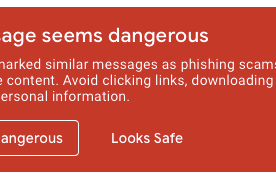
Here's the updated DOOM WARNING that appears on a suspicious message in the new Gmail user interface. But why, I ask, would it appear on this particular message that I recei…
Here's a neat DMARC trick that I would have implemented sooner, had I read MAAWG's " Best Practices for Parked Domains " document a little closer back when it c…